Researchers have observed an increase in attacks deploying the EvilExtractor tool, a data theft software targeting sensitive...
Month: April 2023
Threat Assessment and Risk Assessment (TARA) is a critical process used by organizations to identify, assess, and...
Discover expert tips to bolster your #AWSSecurity and safeguard cloud workloads 🛡️! Learn about IAM policies, Control...
Hacker steals content from Egyptian Quran Karim Radio through piracy program, sells to Arab & Islamic countries....
In today’s world, where work and personal computing are increasingly intertwined, it’s crucial to understand the importance...
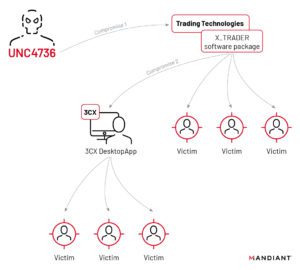
🔓 #3CX hit by a groundbreaking double #SupplyChainAttack! 😲 North Korean hackers target #Crypto businesses via a...
Protect your system from the critical CVE-2023-23397 vulnerability in Microsoft Outlook! Learn how to fix it and...
Improve your software development with CI/CD! Learn how to automate updates and deployments with Kubernetes and popular...
“Collaboration in SaaS can create high-risk situations if links are shared without caution. Learn best practices for...
Microsoft report links Iranian Mint Sandstorm APT to US critical infrastructure attacks, utilizing new tactics and targeting...